Case Studies
CHAMELEON TECHNOLOGY PARTNERS EXPERIENCES IN THE FEDERAL AND COMMERCIAL MARKETS
Case studies illustrate Chameleon Technology Partners strengths
Chameleon Technology Partners' (CTP) successful past performances in Information Security Programs and services make CTP a low risk SDB choice. Our technical focal areas support with scalable, relevant, future‐flexible Content Management, Digital Repositories, Knowledge Discovery, Secured Collaboration and Systems engineering / Enterprise Architecture. Our young, successful history as an IT Firm has registered relevant and successful track record with federal customers. Comparatively, our rated successes surpass the performances of other Small Businesses and Research Groups and separates CTP from its competitors.

Information Security: Confidentiality, Integrity and Availability
With the continuously rising intrusion threats both internal and external, Security managers today are easily overburdened with monitoring, data-collection and administration of security measures. That's why it's more important than ever to coordinate systems, applications and data protection schemes to create a full defense-in-depth approach to information security (INFOSEC) and vulnerability assessment.

In this Federal-Civil Case Study we proposed and delivered applications security improvements to protect sensitive PII (Personally Identifiable Information) constituent data. We initially identified those stakeholders who were collecting, managing or designing an Information Security management plan. They were most accountable for governing, gathering, analyzing, and using systems and sensitive data.
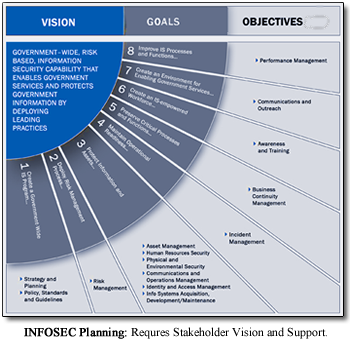
We specifically established rules of conduct to protect the organization from the insider threat. Our Information Security Management Plan contained provisions governing the use and access by all users, systems owners and stakeholders. We provided support of:
-
INFOSEC standards and statutes pertaining to Information Systems use and Access and Identity Management policies and procedures
-
Established User's and stakeholder's rights; information governance
-
Systems Engineering designs and Security Architecture approach
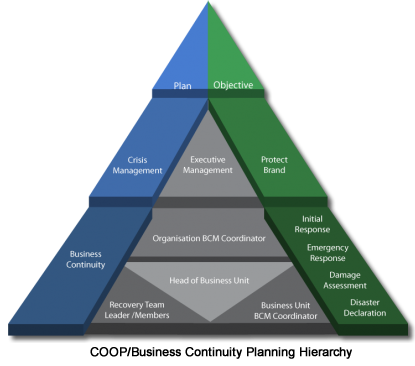
Risk and Concept of Operations Management Planning
Continuity Management Planning
Conducted Engineering design sessions outlining linkages between databases and systems that contained and protected digital data. Establish security criteria for electronic attack vectors
We assisted the enablement of governing elements to sustain an ongoing INFOSEC Program. These INFOSEC efforts strengthened their digital protection posture with both strategic and tactical awareness as well as expert implementation.